Cloud Identity Security
Manage identities before they’re exploited in multi-cloud environments.

Manage an Explosion of Identities
Manage Privileged Access
Ensure all identities only perform actions that are required for their task and nothing more.
Visualize IAM Relationships
Visualize complex, interwoven IAM roles to quickly highlight and prevent over-privileged access to cloud services.
Detect High-Risk Anomalies
Utilize AI to pinpoint unusual access patterns and connect disparate, high-risk anomalies in user behavior.

Enforce Least Privilege
The Sophos IAM visualization tool for Amazon Web Services and Microsoft Azure removes the challenge of managing widespread and interwoven IAM roles, groups, and permissions and helps your teams efficiently enforce least privilege access.
- Use interactive visualizations to understand the relationships between IAM roles, IAM users, and cloud provider services.
- Quickly audit identities with an inventory of IAM users, SSO users, IAM groups, and IAM roles.
- Identify quick wins, including inactive roles and those with multi-factor authentication disabled.
- Prevent external accounts from assuming AWS IAM roles with integration to the AWS IAM Access Analyzer service.
- Automatically identify high-risk, over-privileged AWS IAM roles.

Distinguish Routine Activity from Malicious Activity
Sophos integrates with AWS CloudTrail to build a picture of user-role activity in AWS to identify both accidental changes and malicious activity from compromised roles.
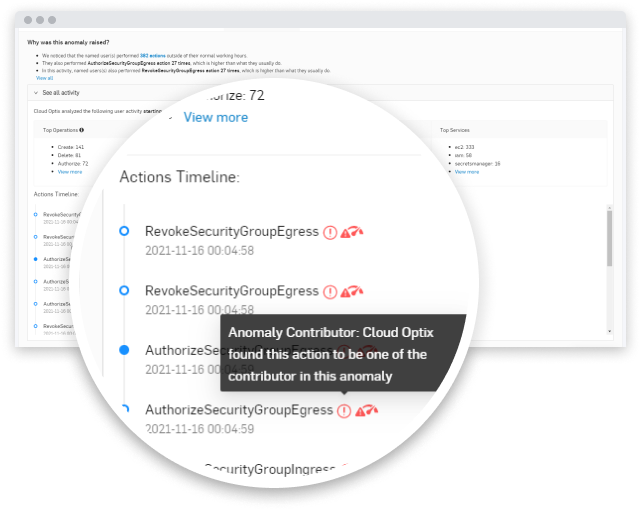
Connect Events with SophosAI
Analyzing one-off user activity is inefficient and overwhelming for security teams. SophosAI breaks through the noise to connect high-risk events and quickly identify compromised user roles.
Focus on High-Risk Patterns of Behavior
Quickly see clear and detailed timeline views of AWS user activities and identify high-risk anomalies, such as actions performed outside of normal working hours and new actions.
Detect and Response to Threats Faster
Remediate identity security incidents faster with risk-assessed and prioritized IAM anomaly alerts alongside all security and compliance issues. Color-coded alerts ensure teams focus on critical issues.
Integrate with DevOps
As DevOps practices increase the pace of change within environments, Sophos reduces risk without losing speed and seamlessly integrates with existing DevOps processes to help prevent breaches.
- Sophos Infrastructure as Code (IaC) template scanning automatically detects misconfigurations, embedded secrets, passwords, and keys pre-deployment.
- Integrate directly with GitHub, Bitbucket, and Jenkins IaC environments or use the REST API as part of your CI/CD pipelines.
- Scan Terraform, AWS CloudFormation, Ansible, Kubernetes, and Azure Resource Manager (ARM) template files.
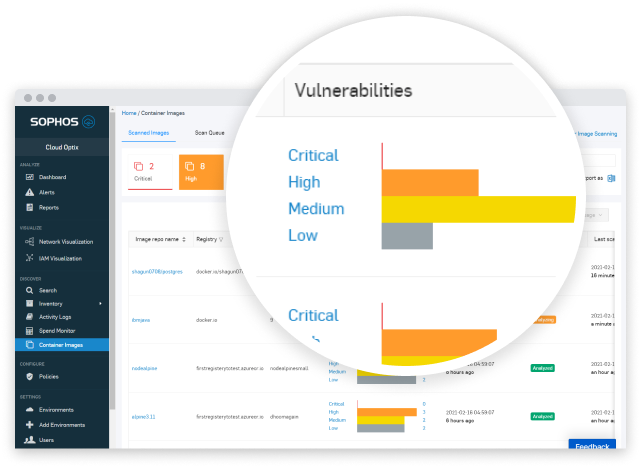
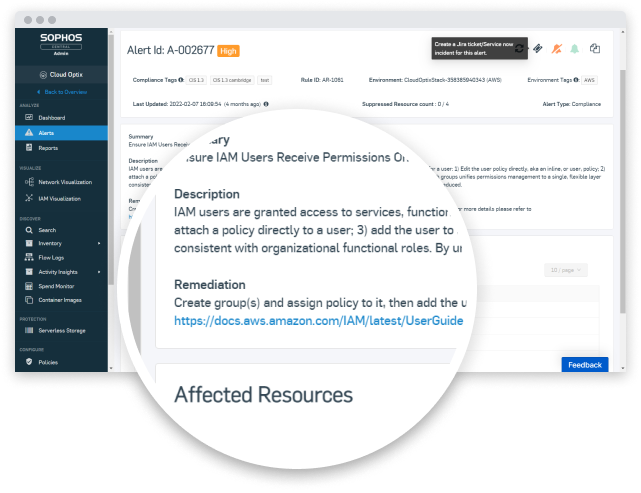
Minimize Time to Detect and Respond
Reduce the complexity of multi-cloud environments with a risk-assessed and prioritized view of identity security, configuration management, and compliance posture.
- Efficiently direct security teams to quick wins and critical issues with color-coded risk alerts.
- Reduce alert fatigue with contextual alerts that group affected resources and provide detailed remediation steps.
- Pinpoint unusual access patterns and locations to identify credential misuse or theft.
- Integrate directly with JIRA and ServiceNow workflow management tools to improve collaboration and reduce remediation time.
Extend Your Data Sources with XDR
Sophos extended detection and response (XDR) is enhanced with cloud environment data to place security teams closer to the occurrence of a security event and offers cross-platform detection capabilities that can provide deep insights and context into issues.
- Use activity log data to search for evidence of AWS and Azure console, APIs, and CLI activity typically associated with attack tactics.
- Use queries associated with attacker tactics to detect initial access, persistence, and privilege escalation.
- Extend visibility across your hybrid cloud estate to investigate cloud workload vulnerabilities and security incidents across firewalls, endpoints, physical services, emails, and more.
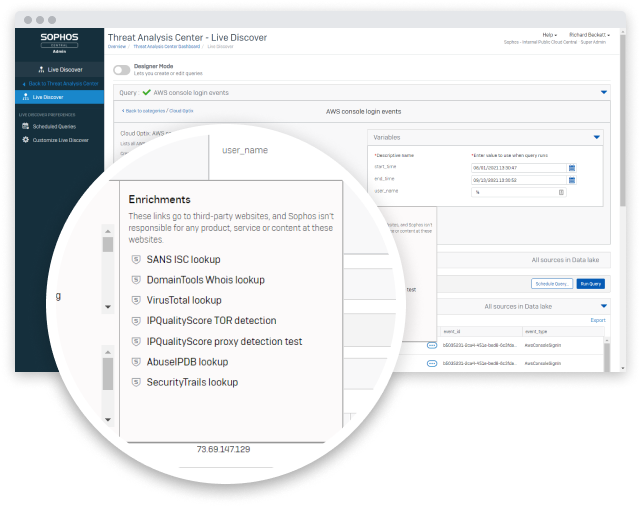

Take the Weight of Cloud Security Off Your Shoulders
Our flexible approach to cybersecurity deployment and management means optimizing security, keeping data secure and private while blocking active threats are goals you can easily achieve.
- Your team can deploy and manage Sophos protection from a single unified console.
- Sophos can connect you with an experienced Sophos Managed Security Partner.
- Sophos Professional Services Team can help with initial deployment.
Respond to Security Incidents at 3 a.m.
The Sophos Managed Detection and Response (MDR) service can work with your team and Sophos MSP, to monitor your environment 24/7/365, and proactively hunt for and remediate threats on your behalf.
- Threat Hunting: The elite team of threat analysts will proactively hunt for threats and help you determine their potential impact and context to your business.
- Response: Initiates actions to remotely disrupt, contain, and neutralize threats on your behalf to stop the most sophisticated threats.
- Continuous Improvement: Get actionable advice for addressing the root cause of recurring incidents to stop them from occurring again.

Delivering Complete Multi-Cloud Security Coverage Across Environments, Workloads, and Identities
Sophos Cloud Native Security is single integrated platform that unifies visibility, governance, and compliance tools with cloud workload protection and entitlements management.
Visibility, Governance, and Compliance
Reduce your attack surface with visibility across multi-cloud environments to detect and remediate security risks and maintain compliance.
Cloud Workload Protection
Protect your infrastructure and data now and as it evolves with flexible host and container workload security for Windows and Linux.
Entitlements Management
Manage identities before they’re exploited with our help to implement least privilege across multi-cloud environments.